Why True RBAC Matters!!
The Case for Snowflake’s Superior Access Control Model
In the evolving landscape of data platforms, Role-Based Access Control (RBAC) has become a critical differentiator. While many platforms offer access control features, few implement true RBAC with the sophistication and elegance of Snowflake. This post explores why proper role-based security architecture matters and demonstrates how Snowflake’s approach surpasses alternatives like Databricks’ group-based model.
The Foundation: Why Databases Need Sophisticated RBAC
The Enterprise Security Challenge
Modern data platforms are the backbone of business intelligence, housing everything from customer data to financial records. The stakes for proper access control have never been higher:
- Regulatory Compliance: GDPR, HIPAA, SOX, and other regulations demand granular access controls
- Data Breach Prevention: Limiting access reduces attack surface and insider threats
- Operational Efficiency: Proper permissions prevent data corruption and unauthorized modifications
- Audit Requirements: Clear permission trails are essential for compliance reporting
Beyond Simple Permissions: The Need for Roles
Individual user permission management becomes unwieldy at scale. Roles provide the abstraction layer that makes enterprise security manageable, auditable, and maintainable.
Roles vs Groups: A Critical Architectural Distinction
The confusion between roles and groups has led many organizations to implement suboptimal security models. Understanding this distinction is crucial for proper RBAC implementation.
Groups: Organizational Identity Containers
Groups represent who users are within an organization:
- Departmental affiliations (Engineering, Sales, HR)
- Geographic locations (US-East, EU-Central, APAC)
- Project teams (DataMigration2024, CustomerAnalytics)
Roles: Functional Permission Containers
Roles define what users can do within the system:
- Data access levels (ReadOnlyAnalyst, DataScientist, DatabaseAdmin)
- Business functions (FinancialReporter, CustomerServiceRep, AuditViewer)
- Technical capabilities (ETLDeveloper, MLModelBuilder, SchemaDesigner)
The Enterprise Advantage of Separation
This architectural separation provides:
- Flexibility: Users can have multiple organizational affiliations and functional roles
- Maintainability: Role permissions can evolve without affecting organizational structure
- Compliance: Clear audit trails separating identity from function
- Scalability: Role-based permissions scale with organizational growth
Databricks Groups: The Limitations of a Hybrid Approach
Databricks attempts to solve access control through groups, but this approach reveals fundamental architectural limitations.
The Databricks Group Model
-- Databricks group creation
CREATE GROUP data_analysts;
CREATE GROUP finance_team;
CREATE GROUP ml_engineers;
-- Permission grants to groups
GRANT SELECT ON schema.customer_data TO data_analysts;
GRANT ALL PRIVILEGES ON schema.financial_data TO finance_team;
GRANT CREATE TABLE ON schema.ml_workspace TO ml_engineers;
-- User assignment
ALTER GROUP data_analysts ADD USER john.doe@company.com;Critical Limitations of the Databricks Approach
Semantic Confusion: Groups serve dual purposes, creating ambiguity between organizational identity and functional permissions. This leads to groups like “finance_team” that mix departmental identity with data access rights.
Limited Flexibility: Users can belong to multiple groups, but there’s no clear hierarchy or inheritance model. This creates permission sprawl and makes it difficult to understand what access a user actually has.
Maintenance Overhead: As organizations grow, the number of groups proliferates exponentially. Without proper role abstraction, administrators must manage an ever-growing matrix of group-to-permission mappings.
Audit Complexity: When groups represent both identity and function, audit trails become convoluted. It’s difficult to answer questions like “Who has access to financial data?” or “What can John Doe actually do?”
Workspace Fragmentation: Many Databricks permissions are workspace-specific, creating silos and inconsistent access patterns across the platform.
Snowflake’s Superior RBAC Architecture
Snowflake implements true RBAC with a sophisticated, enterprise-grade architecture that addresses all the limitations of group-based systems.
The Snowflake Role Model
-- Role creation with clear functional purpose
CREATE ROLE data_analyst;
CREATE ROLE senior_data_analyst;
CREATE ROLE financial_data_reader;
CREATE ROLE customer_data_analyst;
-- Sophisticated role hierarchy
GRANT ROLE data_analyst TO ROLE senior_data_analyst;
GRANT ROLE financial_data_reader TO ROLE senior_data_analyst;
-- Granular permission assignment
GRANT SELECT ON schema.customer_data TO ROLE customer_data_analyst;
GRANT SELECT ON schema.financial_data TO ROLE financial_data_reader;
GRANT CREATE VIEW ON schema.analytics TO ROLE data_analyst;
-- Flexible user-role assignment
GRANT ROLE data_analyst TO USER john.doe;
GRANT ROLE financial_data_reader TO USER john.doe;
GRANT ROLE customer_data_analyst TO USER jane.smith;
-- Dynamic role switching
USE ROLE data_analyst;
USE ROLE financial_data_reader;Snowflake’s Architectural Advantages
True Role Hierarchy: Snowflake supports sophisticated role inheritance, allowing senior roles to inherit permissions from junior roles. This creates a natural progression of access that mirrors organizational structure while maintaining functional clarity.
Multiple Concurrent Roles: Users can hold multiple roles simultaneously and switch between them as needed. This flexibility is essential for modern data professionals who wear multiple hats.
Session-Level Security: The ability to switch roles within a session provides fine-grained security control. Users can operate with minimal permissions by default and elevate only when necessary.
Built-in Governance: Snowflake includes system roles (ACCOUNTADMIN, SYSADMIN, SECURITYADMIN) that provide clear separation of administrative duties, a critical requirement for enterprise governance.
Comprehensive Audit Trail: Every role assignment, permission grant, and role switch is logged, providing complete visibility into who has access to what and when.
Why Snowflake’s Approach Wins: A Detailed Comparison
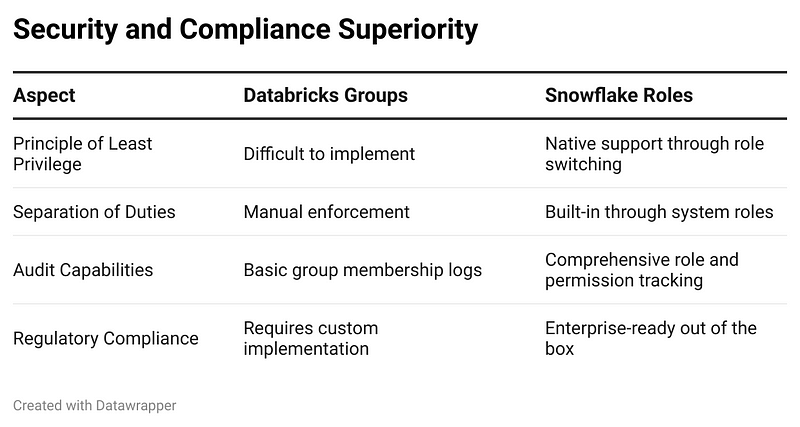
Operational Excellence
Snowflake’s role model reduces administrative overhead through:
- Clear role inheritance reducing permission duplication
- Systematic approach to permission management
- Built-in governance through system roles
- Comprehensive logging and monitoring
Databricks requires significant custom development to achieve similar governance capabilities:
- Custom tooling for permission auditing
- Manual processes for role lifecycle management
- Complex group hierarchies that become unwieldy at scale
Scalability and Flexibility
Snowflake’s architecture scales naturally with organizational growth:
- Role Templates: Standard roles can be replicated across departments
- Dynamic Inheritance: New roles can inherit from existing ones
- Flexible Assignment: Users can be granted roles as needed without restructuring
- Context-Aware Security: Role switching allows appropriate access in different contexts
Real-World Enterprise Scenarios
Scenario 1: Financial Services Compliance A bank needs to ensure that only authorized personnel can access customer financial data, with different levels of access for different roles. Snowflake’s role hierarchy naturally supports this:
CREATE ROLE customer_data_viewer;
CREATE ROLE customer_data_analyst;
CREATE ROLE customer_data_manager;
GRANT ROLE customer_data_viewer TO ROLE customer_data_analyst;
GRANT ROLE customer_data_analyst TO ROLE customer_data_manager;
-- Granular permissions at each level
GRANT SELECT ON customer_basic_info TO ROLE customer_data_viewer;
GRANT SELECT ON customer_financial_details TO ROLE customer_data_analyst;
GRANT ALL PRIVILEGES ON customer_data_schema TO ROLE customer_data_manager;Scenario 2: Multi-Tenant Analytics Platform A company providing analytics services to multiple clients needs to ensure strict data isolation. Snowflake’s role model makes this straightforward:
CREATE ROLE client_a_analyst;
CREATE ROLE client_b_analyst;
CREATE ROLE cross_client_reporter;
-- Client-specific access
GRANT SELECT ON client_a_schema.* TO ROLE client_a_analyst;
GRANT SELECT ON client_b_schema.* TO ROLE client_b_analyst;
-- Aggregated reporting role
GRANT SELECT ON aggregated_reporting_views.* TO ROLE cross_client_reporter;Implementation Best Practices for Snowflake RBAC
Strategic Role Design
- Functional Over Organizational: Design roles around what users do, not where they sit
- Hierarchical Planning: Use role inheritance to minimize permission duplication
- Principle of Least Privilege: Grant minimum necessary permissions, allow elevation as needed
- Role Lifecycle Management: Plan for role creation, modification, and retirement
Operational Excellence
-- Example of well-designed role hierarchy
CREATE ROLE base_user;
CREATE ROLE data_reader;
CREATE ROLE data_analyst;
CREATE ROLE senior_data_analyst;
CREATE ROLE data_manager;
-- Build hierarchy
GRANT ROLE base_user TO ROLE data_reader;
GRANT ROLE data_reader TO ROLE data_analyst;
GRANT ROLE data_analyst TO ROLE senior_data_analyst;
GRANT ROLE senior_data_analyst TO ROLE data_manager;
-- Assign appropriate default roles
ALTER USER john.doe SET DEFAULT_ROLE = data_reader;
ALTER USER jane.smith SET DEFAULT_ROLE = data_analyst;Governance and Monitoring
Snowflake’s superior logging capabilities enable comprehensive governance:
-- Monitor role usage
SELECT * FROM SNOWFLAKE.ACCOUNT_USAGE.QUERY_HISTORY
WHERE ROLE_NAME = 'SENSITIVE_DATA_ANALYST';
-- Audit role assignments
SELECT * FROM SNOWFLAKE.ACCOUNT_USAGE.GRANTS_TO_USERS
WHERE DELETED_ON IS NULL;
-- Track role switching
SELECT * FROM SNOWFLAKE.ACCOUNT_USAGE.SESSIONS
WHERE USER_NAME = 'john.doe';Migration Strategy: Moving from Databricks to Snowflake
Assessment Phase
- Audit Current Groups: Document all existing Databricks groups and their permissions
- Identify Patterns: Distinguish between organizational groups and functional roles
- Map Dependencies: Understand how current permissions support business processes
Design Phase
- Role Architecture: Design Snowflake roles based on business functions, not existing groups
- Hierarchy Planning: Create role inheritance structure that minimizes complexity
- Permission Mapping: Map current group permissions to appropriate Snowflake roles
Implementation Phase
- Parallel Development: Build Snowflake role structure alongside existing Databricks setup
- Incremental Migration: Move teams gradually, validating access patterns
- Comprehensive Testing: Ensure all business processes work with new role structure
The Competitive Advantage of Superior RBAC
Organizations that implement Snowflake’s sophisticated RBAC model gain significant advantages:
Reduced Security Risk: Proper role-based access control significantly reduces the attack surface and insider threat risk.
Improved Compliance Posture: Comprehensive audit trails and built-in governance features simplify regulatory compliance.
Operational Efficiency: Well-designed role hierarchies reduce administrative overhead and improve user productivity.
Business Agility: Flexible role assignment enables rapid response to changing business needs without compromising security.
Cost Optimization: Proper access controls prevent unauthorized resource usage and reduce compliance costs.
Conclusion: The Clear Choice for Enterprise Data Security
While Databricks offers basic access control through groups, Snowflake’s sophisticated RBAC architecture represents the gold standard for enterprise data security. The distinction between identity and function, support for role hierarchies, session-level security, and comprehensive audit capabilities make Snowflake the superior choice for organizations serious about data security and governance.
The initial investment in understanding and implementing Snowflake’s RBAC model pays dividends in reduced security risk, improved compliance posture, and operational efficiency. As data continues to grow in value and regulatory scrutiny intensifies, organizations need access control systems that can scale with their needs while maintaining the highest security standards.
Snowflake’s RBAC architecture isn’t just better than Databricks’ group-based approach — it’s the foundation for enterprise-grade data security in the modern era. Organizations still relying on simpler group-based models are not just missing out on superior functionality; they’re accepting unnecessary security risks and operational complexity that sophisticated RBAC was designed to eliminate.
What’s Next: Our Data Governance Deep-Dive Series
This exploration of RBAC fundamentals is just the beginning of a comprehensive examination of enterprise data governance.
Joel Roland and I will be publishing a multi-part blog series that builds on these RBAC foundations to cover the broader landscape of data governance in modern cloud platforms.
Our upcoming posts will delve into data classification and advanced security patterns. Each post will continue to demonstrate how Snowflake’s architecture provides superior capabilities for enterprise data governance compared to alternative platforms. Stay tuned as we explore how proper RBAC serves as the cornerstone for a comprehensive data governance strategy that scales with your organisation’s needs.

Leave a comment